No matter the size of your business, you are now a target. Cyber-terrorists have found their hobbyhorse and it is called: Ransomware.
With the mention of some attacks in the news, you should be aware that this is no longer a pipe dream but a very real risk. And what you see on the news is just the tip of the iceberg as it represents less than one percent of cases.
According to the CPA Order, in 2017, one in five businesses in Canada suffered a security breach. Imagine what the numbers could be in 2021, following the past two years of turbulence.
So, you think you are safe behind your firewall?
Long before the pandemic, architects were already saying that the “perimeter” model had to be reviewed. It was no longer true that if the stations were all behind a corporate firewall, they were safe. Data had to learn self-defense.
So when the lockdown forced IT departments to allow remote access to those same systems and data, the perimeter paradigm had weathered its first storm.
And whoever says storm, says pirates.
With every social instability, we can see an increase in attacks. The pandemic was no exception and returning to the office could be another opportunity as well.
But what do you mean “one-click away from being destroyed”?
Here are some things that can happen:
- An employee receives an email on his corporate workstation that he believes is legitimate and that looks in every way like an order form from one of your customers. He, therefore, decides to open the PDF attached to this email.
- When opening, the computer seems to have a problem for a minute or two and then everything returns to normal
- In the background, the computer has set up a series of doors and tools for cyber terrorists to gain remote access, despite your firewall, VPN, and other protections.
- A few weeks later, when everyone else logs on, you discover with horror that all your devices have been encrypted without your knowledge overnight. All laptops, computers, and servers are now out of use.
- You hire a team of experts who, if you are amongst the lucky ones, will get you back on your feet within 1 to 3 months depending on the size of your business.
- In the meantime, all your projects are on hold, you have no income, and you have to get your business back on track at your usual costs.
Note that 95% of malware is distributed via email. Of all the SMEs that were the victim of a cyberattack, 60% went out of business within six months of the incident.
You understand that you are probably more vulnerable than you think.
Criminals organize in unions
It is not just the business community that has had to reinvent itself during the pandemic! Cyber terrorists had adopted telecommuting long before the pandemic. The latter only accelerated some of their projects.
What we know about these cyber terrorists:
- They are global organizations, mostly speaking Russian
- They actively recruit via Twitter
- They organize themselves at the level of attacks to resell them as a service
- They set up several levels of attacks, in different countries
It is therefore now possible for a young inexperienced cybercriminal to deploy attacks beyond his knowledge, simply on the promise of profit sharing.
State support for some of these criminal groups
Here is a summary map of known groups supported by certain states (Extract from Microsoft’s cyber defense annual report).
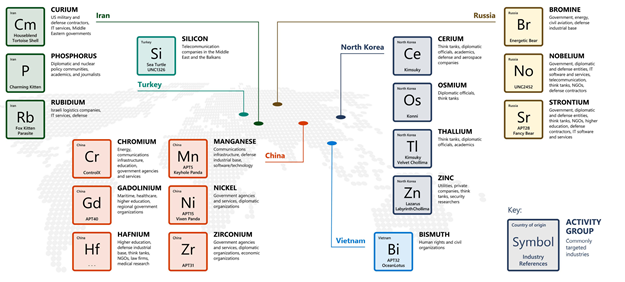
To better understand the situation, there are some sources that you may find helpful:
- Microsoft Digital Defense Report and Security Intelligence Reports
- Canadian Center for Cyber Security
- National Institute of Standards and Technology (NIST)
If you are using Microsoft 365, link your logs to the security center and set up Azure Sentinel. You will get a lot of metrics and clues to improve your situation.
How can I protect myself?
We recommend a multiple vector approach.
- First, train and educate your users
- Set up effective bidirectional filters. It is no longer a matter of protecting yourself against attacks from outside as they can now come from inside your network
- Implement a more robust authentication system, complex passwords, and proof of multi-factor authentication preventing easy access to passwords. Biometrics can be an interesting option.
- Therefore, ancestral services requiring simple passwords or not tolerating multi-factor should be removed or isolated as soon as possible.
- Organize an efficient and centralized collection of your security logs, so you will be able to know the path taken by a cybercriminal, and, with good sources of security information, you can even prevent certain problems by closing existing loopholes.
- Assemble a team of cybersecurity analysts. Even if you accumulate a ton of event logs, without a team to react to the information gathered it becomes pointless.
- Do not hesitate, as with your car, to take out insurance. Build mechanisms that will support you financially if the worst ever happens.
Disbelievers always think that “It only happens to others“
Becoming a father at the age of 15 quickly made me leave the clan of unbelievers. I can assure you that major events with big impacts don’t just happen to others. I have even witnessed attacks targeting irrelevant targets
You should know that the main factor that ensures the profitability of these attacks is the volume.
According to the FBI, and in the United States alone in 2017, there was a computer attack every 40 seconds, and ransomware payments approached $ 1 billion. According to the same study, the business losses caused by these attacks exceeded $ 5 billion (Data Privacy Group report, June 28, 2021).
Extrapolate with all the upheavals of the past two years, today’s numbers easily must have doubled.
Do you think this is alarmist?
Let’s assume that a failure caused by a cyber attack in your company stops your activities for 45 days:
- 45 days without income
- 45 days without access to your emails
- All your projects are on hold
- Your confidential information or even your intellectual property is held hostage
- 45 days to cover the costs of multidisciplinary teams (lawyers, negotiators, technology experts) between 16 and 20 hours per day
- Without forgetting to add crisis management, media and management of public opinion and your customers to maintain your image.
As you can see, the costs are exploding rapidly.
The next steps
Start by making your teams aware, then carry out an external analysis of your current situation, then apply the measures proposed following this analysis.

